Michigan Dominion voting machines and corrupt state officials exposed, Sidney Powell and Sheriff Dar Leaf lawsuits and CISA admission that Dominion is vulnerable
Michigan Dominion voting machines and corrupt state officials exposed, Sidney Powell and Sheriff Dar Leaf lawsuits and CISA admission that Dominion is vulnerable
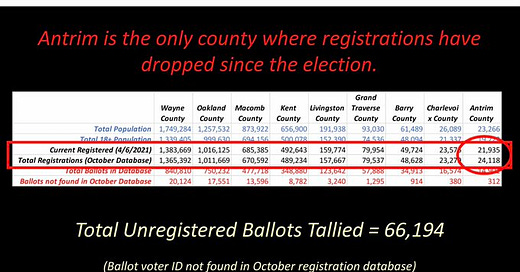
Read the following and draw your own conclusions.
From the Sidney Powell lawsuit filed November 25, 2020.
“10. In deciding to award Dominion a$25 million, ten-year contract (to a Dominion project team led by Kelly Garrett, former Deputy Director of the Michigan Democratic Party), and then certifying Dominion software, Michigan officials disregarded all the concerns that caused Dominion software to be rejected by the Texas Board of elections in 2018 because it was deemed vulnerable to undetected and non-auditable manipulation. An industry expert, Dr. Andrew Appel, Princeton Professor of Computer Science and Election Security Expert has recently observed, with reference to Dominion Voting machines: "I figured out how to make a slightly different computer program that just before the polls were closed, it switches some votes around from one candidate to another. I wrote that computer program into a memory chip and now to hack a voting machine you just need 7 minutes alone with it and a screwdriver."3
11. Plaintiff’s expert witness, Russell James Ramsland, Jr. (Exh. 101, “Ramsland Affidavit”), has concluded that Dominion alone is responsible for the injection, or fabrication, of 289,866 illegal votes in Michigan, that must be disregarded. This is almost twice the number of Mr. Biden’s purported lead in the Michigan vote (without consideration of the additional illegal, ineligible, duplicate or fictitious votes due to the unlawful conduct outlined below), and thus by itself is grounds to set aside the 2020 General Election and grant the declaratory and injunctive relief requested herein.”
Zachary Larsen, Michigan Assistant Attorney General from 2012 through 2020:
“87. The GLJC Complaint alleges the Detroit Election Commission “systematically
processed and counted ballots from voters whose name failed to appear in either the Qualified Voter File (QVF) or in the supplemental sheets.” Exh. 3, GLJC Complaintat 3. The GLJC Complaint provides additional witness affidavits detailing the fraudulent conduct of election workers, in particular, that of Zachary Larsen, who served as a Michigan Assistant Attorney General from 2012 through 2020 and was a certified poll challenger at the TCF Center. “Mr.
Larsen reviewed the running list of scanned in ballots in the computer system, where it appeared that the voter had already been counted as having voted. An official operating the computer then appeared to assign this ballot to a different voter as he observed a completely different name that was added to the list of voters at the bottom of a running tab of processed ballots on the right side
of the screen.” Id. at ¶ 16. Mr. Larsen observed this “practice of assigning names and numbers” to non-eligible voters who did not appear in either the poll book or the supplement poll book. Id. at ¶ 17. Moreover, this appeared to be the case for the majority of the voters whose ballots he personally observed being scanned. Id.”
From constitutional scholar Jonathan Turley November 23, 2020.
“Democratic leaders like Michigan’s Attorney General Dana Nessel have threatened criminal prosecution against those who have posted videos alleging voting fraud and even threatened possible prosecution of legislators who meet with President Trump or raise challenges to the election results. The media is virtually silent on these threats to coerce lawyers and legislators into silence. That is not viewed as a threat to the rule of law. The threats against lawyers follows a pattern where Democratic members are calling for blacklists and others denounce any questioning of the Biden victory as akin to “Holocaust denial.” I spoke last week to Republican lawyers who described death threats, doxxing, and continual harassment for their representation in these lawsuits. The message is that if you represent the wrong side you will be denounced, doxxed, and disbarred.”
Corrupt Judge Parker supports corrupt state officials.
“In a supplemental brief filed in support of their motion for sanctions on April 6, 2021, the State Defendants also identify three specific allegations that they contend were not well-grounded in fact: 1. “‘[T]he absentee voting counts in some counties in Michigan have likely been manipulated by a computer algorithm,’ and [] at some time after the 2016 election, software was installed that programmed tabulating machines to ‘shift a percentage of absentee ballot votes from Trump to Biden.’” 2. “Smartmatic and Dominion were founded by foreign oligarchs and dictators to ensure computerized ballotstuffing and vote manipulation to whatever level was needed to make certain Venezuelan dictator Hugo Chavez never lost another election.” 3. “The several spikes cast solely for Biden could easily be produced in the Dominion system by preloading batches of blank ballots in files such as Write-Ins, then casting them all for Biden using the Override Procedure (to cast Write-In ballots) that is available to the operator of the system.””
Michigan Sheriff Dar Leaf lawsuit filed June 3, 2022.
“35. Defendant Nessel has shown her inherent bias against any fraud claims or suspected criminal acts committed in relation to the investigation of rampant voter fraud that occurred during the November 2020 election, including the suspected hacking and manipulation of voting machines (finally acknowledged by the media). (Exhibit 1, Various Social Media Posts and Publications).
40. In light of these admitted biases and her mockery and disdain for Plaintiff, and all others who point out the now demonstrated problems with voter fraud, illegal ballot harvesting and trafficking, and voting machine hacking, Defendant Nessel is conflicted out and unable to ethically or legally overview, direct, authorize, or otherwise involve herself in any ostensible “investigation” of voter fraud and alleged criminal activity that may have occurred in Barry County, and in the process of that she is nonetheless forbidden from obstructing, interfering with, encroaching upon, or otherwise usurping the exclusive constitutional duties of Plaintiff County Sheriff.”
“46. Defendant Benson has shown her inherent bias against any fraud claims or suspected criminal acts committed in relation to the investigation of rampant voter fraud that occurred during the November 2020 election, including the suspected hacking and manipulation of voting machines (finally acknowledged by the media and as demonstrated in multiple unbiased and impartial expert analyses). (Exhibit 2, Various Social Media Posts and Other Publications).”
48. In light of these admitted biases and her mockery and disdain for Plaintiff, and all others who point out the now demonstrated problems with voter fraud, illegal ballot harvesting and trafficking, and voting machine hacking, Defendant Benson is conflicted out and unable to ethically or legally overview, direct, authorize, or otherwise involve herself in any ostensible “investigation” of voter fraud and alleged criminal activity that may have occurred in Barry County, and in the process of that she is nonetheless forbidden from obstructing, interfering with, encroaching upon, or otherwise usurping the exclusive constitutional duties of Plaintiff County Sheriff.”
US Govt. agency CISA June 3, 2022 report of numerous vulnerabilities in Dominion voting mahines.
“2.2.2 MUTABLE ATTESTATION OR MEASUREMENT REPORTING DATA CWE-1283
The tested version of ImageCast X’s on-screen application hash display feature, audit log export, and application export functionality rely on self-attestation mechanisms. An attacker could leverage this vulnerability to disguise malicious applications on a device.
CVE-2022-1740 has been assigned to this vulnerability.
2.2.3 HIDDEN FUNCTIONALITY CWE-912
The tested version of ImageCast X has a Terminal Emulator application which could be leveraged by an attacker to gain elevated privileges on a device and/or install malicious code.”